Content begins here
Main page content
Click to collapse
Mastering the basics
Click to collapse
Even in an increasingly digital world, the fundamentals of digital literacy are the foundation for successfully navigating in an online environment. This chapter explores the essential skills and knowledge related to legal issues around privacy and security and digital collaboration. This will help you develop basic competencies to effectively use digital technologies.
Digital Communication & Collaboration Click to collapse
Digital Communication and Collaboration
Interaction and communication among students as well as with instructors represent crucial components of working life but also of studying. These exchanges enable collaborative learning through the sharing of professional and life experiences. In online courses, the importance of communication becomes even more apparent. Due to the lack of face-to-face interaction between learners, a sense of isolation can quickly arise. To counteract this and promote networking and collaboration between learners and instructors despite physical (and temporal) distance, certain rules should be followed.
 Communication in virtual space
Communication in virtual space
A distinction is made between two basic types of communication: asynchronous (time-delayed) and synchronous (simultaneous) interaction. The essential characteristics of these two forms are explained below.
| Characteristics | Tools at MCI | |
|---|---|---|
| asynchronous communication | Asynchronous communication is characterized by the fact that it is not simultaneous. This means that participants do not have to be online at fixed times. Instead, the exchange of information is primarily in writing. Here, the non-verbal elements of communication are missing, such as facial expressions and gestures. Flexibility is created by the fact that different writing styles can be used depending on the situation and contributions can be carefully formulated before they are sent. |
Sakai Discussion |
| synchronous communication | Synchronous communication is characterized by all learners being in the same (virtual) room at the same time and exchanging both verbal and written information. By using cameras, aspects of non-verbal communication can be observed. Chat enables (informal) communication. Headset and microphone are necessary to participate in live events, such as a webinar. |
Study (Big Blue Button) |
Online communication has a number of characteristics that affect how we interact. These include:
|
The absence of nonverbal signals Communication is characterized by non-verbal signals such as body language, facial expressions and gestures, as they put words into context and help us to understand the intention behind a message. Para-verbal signals such as voice color and tone of voice are also crucial. Online communication lacks these important non-verbal hints, which is why we often rely on emoticons or abbreviations to partially compensate for them. However, this can affect the interpersonal dynamic because the distance in virtual conversations is greater than in face-to-face conversations. |
"Social Presence" "Social presence" refers to the sense of personal connection and interaction in communication. In working and learning environments, a strong sense of connection can positively influence collaboration and motivation. To achieve a high "social presence" in online settings as well, active participation and contributions to activities are important to make others feel present and engaged. |
Dealing with inappropriate behavior Studies have shown that some people behave less politely and inappropriately in online interactions. This is probably due to the assumption of anonymity. Such behavior can lead to aggression and negative manifestations such as bullying, stalking, racism and sexism. In most cases, this anonymity does not exist. Inappropriate behavior should not be tolerated, just as in personal interactions, and necessary consequences should be initiated. |
 Netiquette
Netiquette
It is particularly important to establish rules for online communication, also known as netiquette. These rules act as a guide for responsible and efficient interaction in the virtual space. They help set standards for dealing with each other and establish a common learning culture in the online community.
The current MCI Netiquette can be found here!
-
 Collaboration in virtual teams
Collaboration in virtual teams
In your studies, you will not only collaborate in the face-to-face phases, but you will also have to do group work in the online phases. Thus, you will work in a so-called "virtual team". It is quite possible that you have already gained or will gain experience with virtual teams in your job as well. In this section, we will look at the specifics of online group work, briefly highlighting the characteristics and success factors of virtual teams, and then consider how technologies can be used to collaborate effectively in this context.
Characteristics of virtual teams:
Virtual teams, whethter in academia or at work, are characterized by the following:
-
They are a group of individuals working towards a common goal
-
They are typically geographically dislocated
-
They use information and communication technologies to enable collaboration
-
They are all responsible for achieving the common goal
-
The duration of virtual team collaboration is often limited
Success factors:
The success of virtual teams depends on, among other things,
-
whether there are clear (ideally written) guidelines for the team's work
-
the extent to which the common goal and the path to achieving it are understood (equally) by everyone and are also documented
-
how well the team succeeds in networking and communicating in the online space, and in exchanging all necessary information and knowledge
-
how efficiently the team members use the available technologies to work together
-
the extent to which there is a good working culture and a basis of trust within the team. This can be a particularly big challenge for virtual teams.
 Technologies for (virtual) collaboration
Technologies for (virtual) collaboration
Of course, the same success factors apply to virtual teams as to all other teams. Especially for the work of team members who are physically separated, technologies for collaboration are needed: In the following you will find a summary of common programs for (virtual) teamwork:
|
Communication |
|
|
File sharing |
|
| Collaborative document editing | |
|
Productivity |
Privacy & Security Click to collapse
Privacy & Security
The right to data protection is a fundamental right and refers to the protection of one's own personal data. This includes personal data, such as name, date of birth or address, which allow you to be precisely identified as a person. Very sensitive data is also health information or information about political opinions, which are considered particularly worthy of protection.
Data protection is legally regulated in the EU General Data Protection Regulation (GDPR) and the Data Protection Act (DPA). Specifically, this means that personal data may only be processed and stored with the consent of the person concerned. Thus, every individual also has the right to know which personal data is processed by third parties.
Since a lot of data is also stored unconsciously on the Internet in particular, it is important to protect one's own personal data or to deal with one's own "Internet identity" on a regular basis. In this way, attacks on privacy, which can lead to negative consequences, can be avoided. In principle, data protection on the Internet is of particular concern:
-
Generation of secure passwords
-
Proctecting one's own computer/laptop
-
Dealing with social media
-
Use of public computers
-
Copyrights on documents and images
At Cybersecurity Guide you can find tips and tricks for protecting personal data on the Internet. There you can find a list of instructions on how to protect your personal data on the Internet and other interesting information.
 Passwords
Passwords
Although the topic of Internet security is heavily discussed, "123456" or "password" are still considered to be the most commonly issued passwords worldwide. However, these can be hacked very quickly, putting private data at risk. Because only a good password can properly protect accounts and profiles. But how do I generate secure passwords? What rules should I follow?
-
Generally, very strong passwords consist of upper and lower case letters, numbers and special characters.
-
The more different characters are used and the longer the password, the better. A very strong password consists of at least 16 characters.
-
Avoid pet or friend names, birth dates, nuber sequences (e. g. 12345), and keyborad patterns (e. g. qwertz) as they are easy to predict.
-
The combination of four different and random words, which are separated by numbers and special characters, is suited (e. g. rubber?3lemon?3 parents?3parrot).
-
In addition, activate the two-factor authentification, i. e. in addition to the username and password also an access code, which is sent via text message or e-mail, is necessary.
-
Use a separatae password for each account.
-
Write down your passwords, but not on your phone or computer (preferable on a piece of paper!).
This TED-Talk provides more insights into password security!
 Further literature
Further literature
Copyright Click to collapse
Copyright
Copyright is included in Article 27 of the Universal Declaration of Human Rights (Resolution 217 A (III), UN General Assembly, 10.12.1948) and states:
- Everyone has the right freely to participate in the cultural life of the community, to enjoy the arts and to share in scientific advancement and its benefits.
- Everyone has the right to the protection of the moral and material interests resulting from any scientific, literary or artistic production of which he is the author.
Copyright refers to all intellectual property, such as literature, music, photography or films. The author has the right of exploitation, i.e. these persons may determine who may use and edit the intellectual property to what extent.
Please activate the english subtitles and watch the video below!
Copyright violation therefore occurs when protected works (especially from the Internet) are reused without consent. Especially in the case of photos in which other people are (recognizably) depicted, the consent of these people is required, e.g. with regard to uploading to social media, even if they did not take the photo themselves.
This can quickly lead to problems, as copyright law is handled differently in different countries. A solution to this is offered by the so-called Creative Commons licenses - CC licenses for short. They authorize third parties to use images, texts or music under certain conditions.
 Creative Commons - which CC licenses are available?
Creative Commons - which CC licenses are available?
|
Attribution
|
The materials may be used and edited if the author is mentioned. |
|
Attribution - sharing under the same conditions
|
Materials may be reused and edited if the author is credited and adaptations must be licensed under the same terms. It is also
|
|
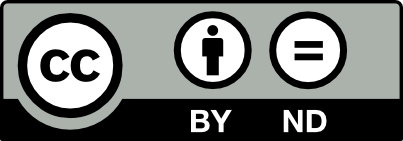
Attribution - no editing
|
The material may be reused if the author is credited. However, the material may not be edited. |
|
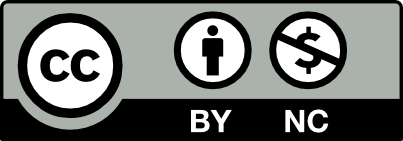
Attribution - non-commercial
|
The material may be reused and edited if the author is credited, but only for non-commerical purposes. The new material do not have to be licensed under the same conditions. |
|
Attribution - non-comercial - Sharing under the same conditions
|
The material may be reused and edited if the author is credited, but only for non-commerical purposes. The new material must be licensed under the same conditions. |
|
Attribution -non-commerical - no editing
|
The material may be downloaded and redistributed only with attribution to the author(s), but may not be edited or used commercially. |
|
Public Domain
|
For material under this license, authors have assigned all copyrights fto the material, meaning that they may be redistributed and edited without conditions. |
For more information, please visit the official website of CreativeCommons.
Open Educational Resources (OERs) Click to collapse
Open Educational Resources (OERs)
There are many materials on the Internet that are particularly suitable for teaching or studying in an educational context. The question often arises as to whether these materials can be used without any problems.
Open Educational Resources (OER) are teaching and learning materials that are freely available on the Internet. They can be used without permission - so they count as CC-licensed materials. For example, these can be:
-
Textbooks
-
course slides
-
Podcasts
-
Online courses (MOOCs)
-
videos….
 Collection of sources
Collection of sources
Here you can find a collection of possible sources for OER materials:
|
Materials, textbooks and online courses |
|
|
Videos |
|
|
Pictures |
|
|
Audios |
|
|
OER searching engine |